Introduction
In the era of cloud computing, understanding cloud security is crucial. This blog post explores the basics of AWS cloud security, guided by the AWS Well-Architected Framework’s Security Pillar.
AWS Well-Architected Framework and the Security Pillar
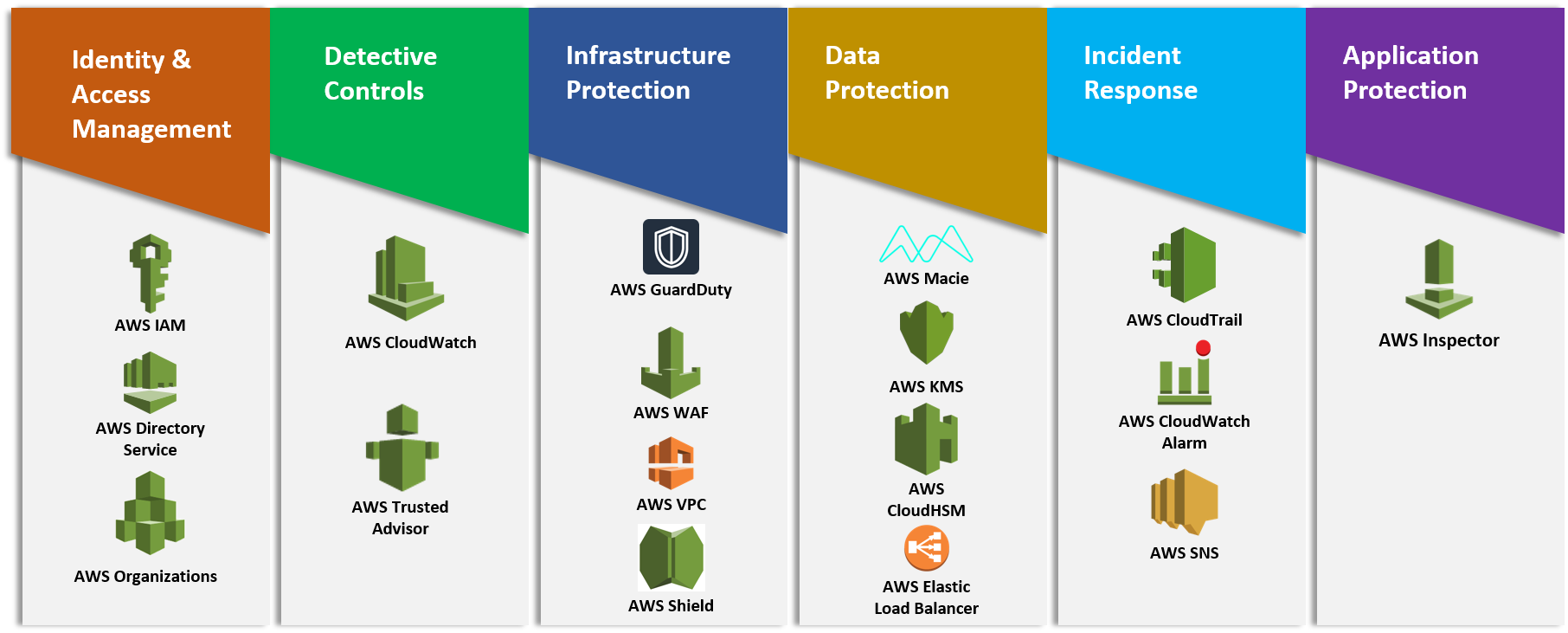
The AWS Well-Architected Framework is a guide to building secure and high-performing infrastructures. Among its five pillars, we’ll focus on the Security Pillar, which protects information and systems. Key areas include identity and access management, data protection, infrastructure protection, detection, incident response, and application security.
Key Areas of the AWS Security Pillar
Let’s examine each key area:
1. Identity and Access Management
Identity and Access Management (IAM) is an integral part of cloud security, focusing on managing who can access your resources, when, and for what purpose.
Key points to note:
- Authentication: Verifying the identity of a user, process, or system. It’s crucial to have strong authentication mechanisms in place, such as multi-factor authentication (MFA).
- Authorization: Determining what permissions authenticated users have, what actions they can perform, and what resources they can access.
- Principle of Least Privilege (PoLP): Granting only the minimum permissions necessary to perform a task.
- Identity Federation: It allows external identities (like from your corporate directory) to be used to manage access to your AWS resources.
- Access Management: Managing how authenticated users are authorized to access resources.
Examples:
- AWS IAM: You can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources.
- AWS Organizations: You can centrally manage and enforce policies for multiple AWS accounts.
High-Level Implementation Practices:
- Enable MFA: Always enable Multi-Factor Authentication for your AWS root account and for any IAM users with console access.
- Use IAM roles: Use IAM roles for applications that run on Amazon EC2 instances.
- Regularly review IAM policies: Frequently review and adjust IAM policies to match the changing needs of your users and to remove unnecessary permissions.
- Implement segregation of duties: Implement separation of duties where necessary to minimize the risk of malicious activity.
This introduction to IAM provides a baseline understanding, but there’s more to learn as IAM is a broad topic and a critical component of the AWS Well-Architected Framework’s Security pillar. We’ll explore more in-depth in future posts.
2. Data Protection
Data protection is a crucial aspect of cloud security, ensuring that your data, whether at rest or in transit, is safeguarded against unauthorized access, breaches, and losses.
Key points to note:
- Encryption: It’s the method of converting data into a code to prevent unauthorized access. Both data at rest and data in transit should be encrypted.
- Key Management: This refers to the administration of cryptographic keys. It’s essential to ensure that the keys are stored and managed securely.
- Access Control: This involves defining who has access to your data. It’s crucial to set strict access controls and regularly review them.
- Data Classification: It’s the process of categorizing your data based on its sensitivity. This helps to apply appropriate security controls.
- Backup and Recovery: Regular backup of your data is crucial to recover from data loss or breaches.
Examples:
- AWS Key Management Service (KMS): It helps you create and manage cryptographic keys to control access to your data.
- Amazon S3 versioning: It helps to preserve, retrieve, and restore every version of every object in your Amazon S3 bucket, which is useful for backup and recovery.
High-Level Implementation Practices:
- Use AWS’s built-in encryption services: Make use of the encryption features provided by AWS to secure data at rest and in transit.
- Regularly backup your data: Always have a backup of your data. Use services like Amazon S3 for storing your backups securely.
- Classify your data: Understand the sensitivity of your data and classify it accordingly to ensure appropriate security measures.
- Limit access to your data: Implement strict access controls. Only give access to those who absolutely need it.
This is a basic introduction to data protection, and there’s more to it as you delve deeper. Data protection forms a significant part of the AWS Well-Architected Framework’s Security pillar, which we’ll discuss more in the future posts.
3. Infrastructure Protection
Infrastructure protection involves adding security measures to your cloud resources to guard against breaches and attacks. This could range from protecting your network to securing your virtual machines and databases.
Key points to note:
- Firewalls: Firewalls act as a shield between your trusted internal network and untrusted external networks. Services like AWS Shield provide managed DDoS protection.
- Access Control Lists (ACLs): These act as a network filter, controlling inbound and outbound traffic to your network.
- Security Groups: They function as virtual firewalls for your instance to control inbound and outbound traffic.
- Virtual Private Networks (VPNs): VPNs provide secure and private connections to a network over the internet, which is particularly important when transmitting sensitive information.
- Endpoint Protection: This aims at securing endpoints or entry points of end-user devices like computers and mobile devices from being exploited by malicious actors and campaigns.
- DDoS Protection: DDoS protection measures are crucial to ensure your services remain available during a distributed denial of service attack.
- Web Application Firewalls (WAF): A firewall that monitors, filters, or blocks the HTTP traffic to and from a web application. It protects against certain types of attacks such as cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection.
Examples:
- Amazon VPC allows you to provision a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define.
- AWS Shield provides managed DDoS protection, safeguarding applications running on AWS.
High-Level Implementation Practices:
- Ensure that all of your resources, like servers and databases, are running in a VPC.
- Regularly update and patch your systems and applications to protect them from vulnerabilities.
- Encrypt data in transit to ensure its integrity and confidentiality.
- Regularly review and tightly manage your security groups. Avoid leaving unused security groups open, which can create unnecessary vulnerabilities.
- Keep all your software up-to-date with the latest patches. This includes not only your applications but also the underlying OS, and any software dependencies your applications may have.
- Segregate your networks based on the sensitivity of the information they handle. For instance, keep development and production environments completely separate.
Remember, this is only an introduction to infrastructure protection. It forms a crucial part of the AWS well-architected framework’s security pillar, which we’ll delve deeper into in future articles. Protecting your infrastructure is an ongoing task and demands consistent reviews and improvements to keep pace with evolving threats.
4. Detection
Detection in cloud security involves identifying unusual or unauthorized activities or anomalies that could indicate a security threat within your cloud environment.
Key points to note:
- Continuous Monitoring: Keep track of what’s happening in your environment. AWS CloudTrail, for example, enables governance, compliance, operational auditing, and risk auditing of your AWS account.
- Alerts: Set up automatic notifications for any anomalous activities. Services like Amazon CloudWatch can be used to collect monitoring and operational data in the form of logs, metrics, and events, providing you with a unified view of AWS resources, applications, and services.
- Threat Intelligence: Keep abreast of the latest security threats and use this information to prepare your cloud environment.
Examples:
- AWS GuardDuty is a threat detection service that continuously monitors for malicious or unauthorized behavior to help protect your AWS accounts and workloads.
- AWS Security Hub gives you a comprehensive view of your high-priority security alerts and security status across your AWS accounts.
High-Level Implementation Practices:
- Regularly analyze security logs and use anomaly detection methods to detect unusual behavior.
- Implement incident response simulations to test your detection tools and ensure they’re functioning as intended.
- Have a plan in place for when a security event occurs, ensuring quick detection leads to effective response.
Remember, this is just a basic primer on detection. It is an integral part of the AWS well-architected framework’s security pillar, which we’ll unpack more thoroughly in future articles. It’s an ongoing process, requiring continuous review and adjustment as new threats emerge.
5. Incident Response
Responding effectively to security incidents is a critical part of cloud security. When security breaches or threats are identified, your ability to react quickly can significantly mitigate any potential damage.
Key points to note:
- Plan for Incidents: AWS provides tools such as AWS Security Hub and Amazon CloudWatch to facilitate rapid detection and response to security incidents. The Security Hub gives a comprehensive view of high-priority security alerts and compliance statuses, while CloudWatch helps collect and monitor operational data.
- Automate Responses: AWS Lambda, a serverless computing service, can help automate the response to certain security triggers, reducing the time between detection and response.
- Iterate and Improve: Post-incident analysis is critical for continuous improvement. Learn from each incident, and adjust your strategies accordingly.
Examples:
- With CloudWatch, you can set alarms to notify you when particular thresholds are breached, allowing for quick response times.
- AWS Security Hub aggregates security findings from various services, giving a broad overview of security status and highlighting areas requiring immediate attention.
High-Level Implementation Practices:
- Define and document your incident response strategy, including roles and responsibilities, communication strategies, and processes.
- Regularly test and refine your incident response plan to ensure it remains effective as your system evolves.
- Utilize automation wherever possible to ensur
6. Application Security
Application security is a critical part of cloud security that focuses on the software and services in your cloud environment. It aims to prevent data or code within the app from being stolen or hijacked.
Key points to note:
- Secure Code: Code should be written with security in mind, following best practices to minimize vulnerabilities. Tools like AWS CodeStar and CodeCommit can help manage secure code development and deployment.
- Input Validation: Always validate, sanitize, and limit user input within your applications to prevent common vulnerabilities such as SQL injection and cross-site scripting (XSS).
- Encryption: Encrypt data both in transit and at rest. AWS provides several services like AWS Certificate Manager for managing SSL/TLS certificates and AWS Key Management Service for creating and managing encryption keys.
Examples:
- You can use AWS WAF (Web Application Firewall) to protect your applications from common web exploits.
- Amazon Macie uses machine learning to automatically discover, classify, and protect sensitive data like Personally Identifiable Information (PII).
High-Level Implementation Practices:
- Adhere to the principle of least privilege in application access control. Only grant the necessary permissions required to perform a function.
- Regularly update and patch your applications to protect against known vulnerabilities.
- Implement monitoring and logging to detect any abnormal behavior or breaches in your applications.
Bear in mind, this is a very basic overview of application security. It’s a key component of the AWS well-architected framework’s security pillar, which we will explore in more depth in future posts. This should serve as a solid foundation to get you started on the journey to robust application security.
Conclusion
The AWS Well-Architected Framework’s Security Pillar provides a strong blueprint for AWS security. We’ve just skimmed the surface; stay tuned for deep dives into each topic in upcoming posts.

0 Comments